Is Storage Snapshot Enough for Data Protection?
Is Remote Data Replication Truly Foolproof?
Does Every Piece of Data Require Real-Time Protection?
In today’s digital era, data has become one of the most valuable assets for enterprises. Whether in finance, healthcare, manufacturing, or the internet industry, efficient data protection and management are essential.
Enterprise data protection relies on three core technologies: data replication, snapshots, and backup. But what are their differences? How do they function? And how should businesses combine them for optimal protection?
Data Replication: Real-Time Synchronization for Data Consistency
Data replication refers to real-time or near-real-time copying of data from one storage device to another.
At its core, data replication ensures multiple copies of data remain highly consistent by transferring data across different storage nodes in real-time. It plays a crucial role in disaster recovery and business continuity, allowing seamless failover to backup nodes in case of primary node failure.
Advantages:
-
High Real-Time Performance: Data is synchronized to the backup system almost instantly.
-
Disaster Recovery: The backup node can quickly take over business operations in the event of a primary system failure, ensuring continuous operation.
Use Cases:
Ideal for applications requiring high data consistency and real-time processing, such as online transactions, financial systems, and e-commerce platforms.
Snapshot Technology: Capturing Moments for Rapid Recovery
Snapshot technology records the state of a storage system at a specific point in time, creating an instantaneous image of the data.
There are two main types of snapshots: Copy-on-Write (COW) and Redirect-on-Write (ROW). By capturing the state of a storage device at a given time, snapshots provide a lightweight form of data protection. In cases of accidental deletion, misoperation, or application crashes, snapshots enable near-instant data recovery.
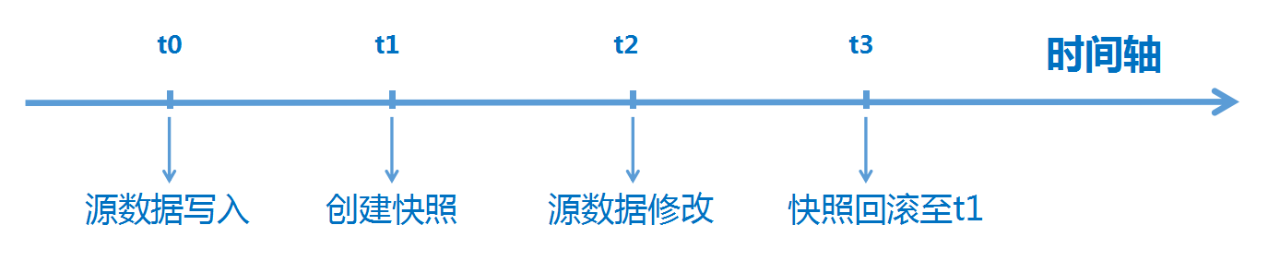
Advantages:
-
Efficiency: Snapshots are created quickly without affecting active systems.
-
Flexible Recovery: Enables quick restoration to a specific time point, making it easier to troubleshoot issues or roll back operations.
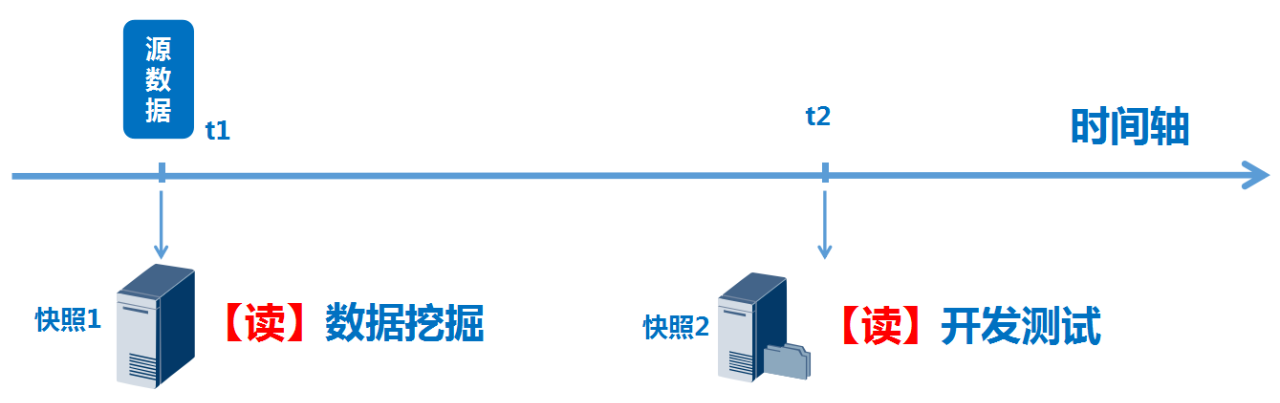
Use Cases:
Commonly used in virtual machines, database systems, and file systems. Particularly suitable for scenarios requiring frequent environment restoration and protection against human errors.
Backup: Long-Term Data Protection and Recovery
Backup involves creating complete or partial copies of data and storing them offsite or on offline media to prevent data loss.
As one of the most traditional yet reliable data protection methods, backup ensures an independent copy of the original data. Backup strategies often include full backups, incremental backups, and differential backups.
Advantages:
-
Data Integrity: Ensures historical data is not lost and can be fully restored after disasters.
-
Flexibility: Different backup strategies can be tailored based on data change frequency and recovery needs.
Use Cases:
Ideal for long-term data retention and regulatory compliance, especially useful for recovering from accidental deletions or system crashes.
Choosing the Right Data Protection Strategy
By now, it’s clear that data replication, snapshots, and backup serve different purposes:
-
Replication focuses on real-time synchronization for disaster recovery and high availability.
-
Snapshots capture the current state efficiently, enabling frequent recovery and testing.
-
Backup provides layered historical protection for long-term data retention and disaster recovery.
Enterprises should evaluate their business needs, data update frequency, system performance, and disaster recovery requirements to formulate an optimal data protection strategy. By integrating these technologies strategically, businesses can build an impenetrable data security fortress.
For instance:
-
If basic data retention and recovery is the goal, a snapshot + backup combination is ideal.
-
If minimizing downtime is critical, data replication is essential to ensure continuous business operations.
AI-Powered Data Protection Solutions for the Future
As data security and high availability demands continue to rise, Information2 leverages its three core data replication technologies to deliver disaster recovery, high availability, and backup solutions. These solutions help enterprises establish an unbreakable defense, ensuring data safety in the digital transformation era.
Data Backup and Recovery
i2Backup provides centralized backup management for diverse data sources, integrating LAN-free backup strategies and deduplication compression for efficiency. With storage-level ransomware protection and NetBackup (NBU) strategy migration, it enables unified control across multiple centers and storage units. Cross-domain cascading replication and backup policy version tracking ensure historical rule modifications are recorded for easy auditing. Supporting D2D2T (Disk-to-Disk-to-Tape) with automated tape archiving, i2Backup delivers exceptional PB-scale backup performance for large-scale data archiving.
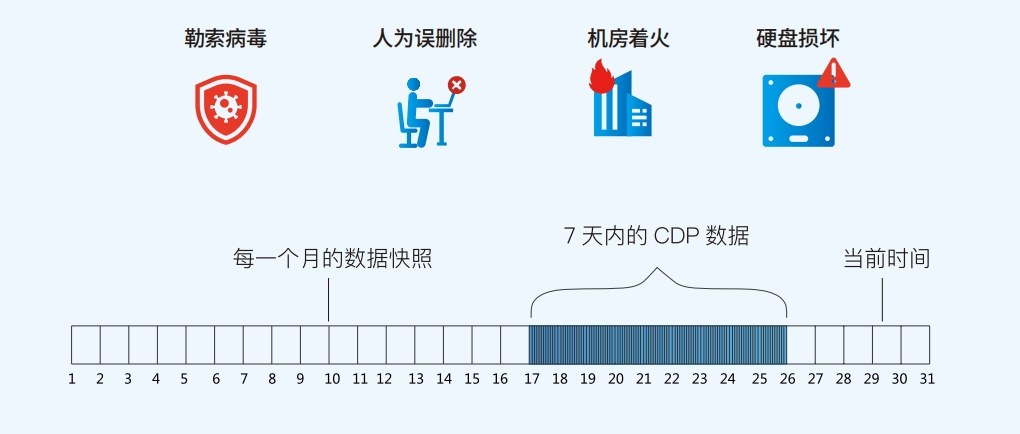
Continuous Data Protection (CDP)
i2CDP offers byte-level replication for uninterrupted protection of critical data. It logs and saves every data change in real-time. In the event of accidental deletion or ransomware infection, users can restore data to any point before the incident with precision down to a fraction of a second.
Real-Time Data Replication
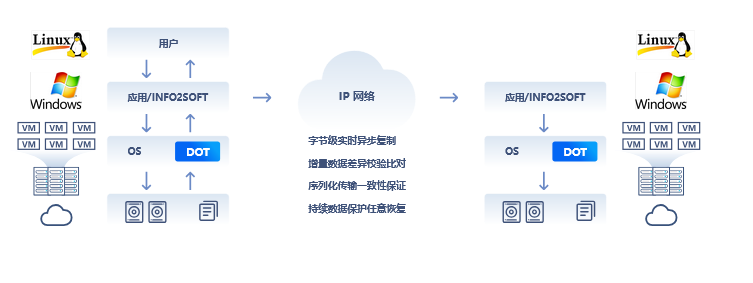
i2COOPY utilizes data serialization transmission to ensure strict data consistency and integrity between production and target systems. Built on Information2’s proprietary byte-level replication technology, it captures new data at the byte level, ensuring high real-time performance with minimal resource consumption. It operates seamlessly across heterogeneous environments, supporting diverse storage hardware and virtual/physical infrastructures for efficient data replication.
A Decade of Innovation: Leading the Industry in Data Protection
With over a decade of expertise, Information2 remains committed to technological innovation, establishing a comprehensive data management ecosystem across finance, government, healthcare, education, and energy sectors.
To address enterprise data security challenges and data silos in intelligent transformation, Information2 has pioneered AI-enhanced data protection solutions. Built on DeepSeek, Qwen, and other intelligent frameworks, these solutions:
-
Intelligently predict potential risk points
-
Dynamically optimize backup strategies
-
Enable second-level emergency response
By integrating AI-driven automation and intelligent document collaboration, Information2 delivers end-to-end lifecycle protection for enterprise data assets, ensuring data safety in the AI era.


 Disaster Recovery Product
Disaster Recovery Product Backups Product
Backups Product Big Data Product
Big Data Product Cloud Data Management
Cloud Data Management







 60-Day Free Trial
60-Day Free Trial







