In the wave of digital transformation, enterprise document management faces unprecedented challenges and opportunities. Decentralized storage, complex permission management, and potential security risks are testing the resilience of enterprises.
-
Documents scattered across shared directories, external hard drives, FTP servers, personal cloud storage, and other locations make efficient management and collaboration difficult.
-
Issues such as ransomware, accidental deletions, and other security threats can lead to document loss or damage, posing serious risks to data integrity.
-
Chaotic document version management and lack of effective permission controls result in inefficiencies.
-
Documents are not effectively retained or utilized, hindering the development of an enterprise knowledge base.
To address these challenges, i2Share File Sharing and Management Platform leverages Information2’s file-level data capture technology and continuous data protection mechanisms, with a core focus on “security” and “convenience,” provides a one-stop solution to meet the diverse needs of the digital era, spanning file storage, security, collaboration, and knowledge mining.
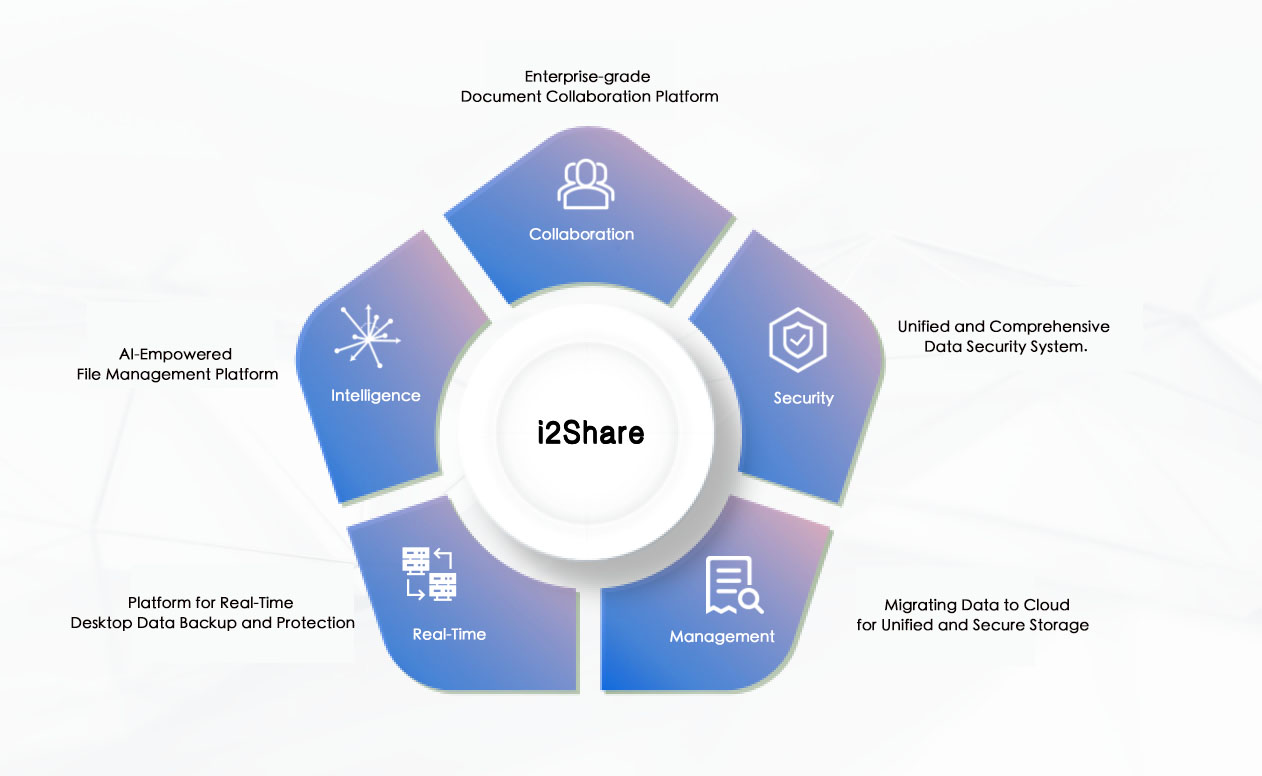
Product Highlight Features
Full Lifecycle Management, Enhanced Efficiency
-
Lifecycle Management from Storage to Deletion: Comprehensive coverage of file storage, access, version control, transfer, recovery, and auditing.
-
Unified Management: Centralized control over distributed files, simplifying the complexity of decentralized storage.
Efficient Collaboration, Optimized Team Productivity
-
Real-time Sharing and Collaboration: Supports multi-user online editing, document commenting, and group discussions, enhancing team collaboration efficiency.
-
Granular Permission Management: Ensures data security during collaboration through role-based permissions and outbound approval processes.
Data Security Assurance, Digital Defense
-
Robust Security Mechanisms: Combines sliced storage and encrypted transmission technology with real-time virus scanning to prevent file leaks and malicious attacks.
-
Continuous Data Protection (CDP) and Version Control: Supports one-click recovery of historical versions, addressing accidental deletions and ransomware threats.
Mobile Office, Flexible Business Response
-
Anytime, Anywhere Access: Supports mobile file preview, editing, and sharing, enhancing remote work efficiency.
-
Cross-Platform Compatibility: Supports multiple operating systems and devices, meeting enterprise needs across various scenarios.
AI Empowerment, Unlocking Knowledge Management Potential
-
Intelligent Semantic Search: Quickly locates file information through natural language understanding, improving search efficiency.
-
Knowledge Base Construction: Transforms documents into valuable enterprise knowledge assets, supporting semantic Q&A and intelligent analysis to aid in decision-making.
Core Application Scenarios
Scenario 1: File Sharing and Management – Redefining the Collaboration Experience
Pain Points:
-
Files scattered across multiple devices and systems with complex permission management.
-
Chaotic document versions and inefficient multi-user collaboration.
i2Share Solution:
-
Supports multi-node deployment architecture for unified management and permission control.
-
Integrates OA approval processes for granular outbound control.
-
Provides real-time virus scanning and full-directory historical version recovery, eliminating file loss risks.
Typical Case:
A shipping group with multiple business areas and cross-regional production bases had internally scattered documents and data across different departments and branches. By leveraging i2Share, they achieved breakthroughs in multi-location collaboration and document management, providing reliable support for their business operations.
Scenario 2: Endpoint Data Protection – Immune to Data Threats
Pain Points:
-
Data loss due to employee accidental deletions or ransomware attacks.
-
Lack of file security protection mechanisms after desktop virtualization.
i2Share Solution:
-
Provides real-time backup and Continuous Data Protection (CDP) for desktop files, supporting one-click and batch recovery.
-
Independently stores and manages virtual desktop files, preventing virus spread and data leaks.
-
Offers flexible permission control and audit log functionality, enhancing compliance and security.
Typical Case:
A provincial maternity and child healthcare hospital utilized i2Share to provide desktop file protection for over 1,000 employees. By combining real-time backup and object storage, the hospital significantly reduced operational costs while effectively addressing ransomware threats.





 10-Day Free Trial
10-Day Free Trial







